Detecting NTDS.dit Dumping
In this blog post, we’ll dive into how attackers use NTDSUTIL to dump the NTDS.dit file, and how you, as a defender, can detect this activity by spotting the creation of two suspicious folders: “Active Directory” and “registry”.
What is NTDS.dit, and Why Do Attackers Want It?
Before we get into the details of detection, let’s talk about why NTDS.dit is such a big deal. The NTDS.dit file is the database that stores all Active Directory data, including:
- User accounts and their password hashes (NTLM and Kerberos)
- Group memberships
- Trust relationships between domains
- And much more
If an attacker gets their hands on this file, they can extract password hashes, perform offline brute-force attacks, and potentially gain control over the entire domain. It’s like giving them the keys to the kingdom.
NTDSUTIL is a legitimate command-line tool used by system administrators to manage Active Directory. However, attackers can abuse it to create a backup of the NTDS.dit file. Here’s how they do it:
ntdsutil "ac i ntds" "ifm" "create full c:\temp" q q
- Gain Elevated Privileges: The attacker needs administrative privileges on the Domain Controller to run NTDSUTIL.
- Create a Snapshot: They use NTDSUTIL to create a snapshot of the Active Directory database.
- Mount the Snapshot: The snapshot is mounted as a virtual disk.
- Copy NTDS.dit: The attacker then copies the NTDS.dit file from the snapshot to a location of their choice.
- Extract Hashes: Finally, they use tools like
secretsdump.pyfrom Impacket to extract password hashes from the NTDS.dit file.
But here’s the kicker: during this process, NTDSUTIL creates two folders that can serve as a telltale sign of malicious activity: “Active Directory” and “registry”.
The Smoking Gun: “Active Directory” and “registry” Folders
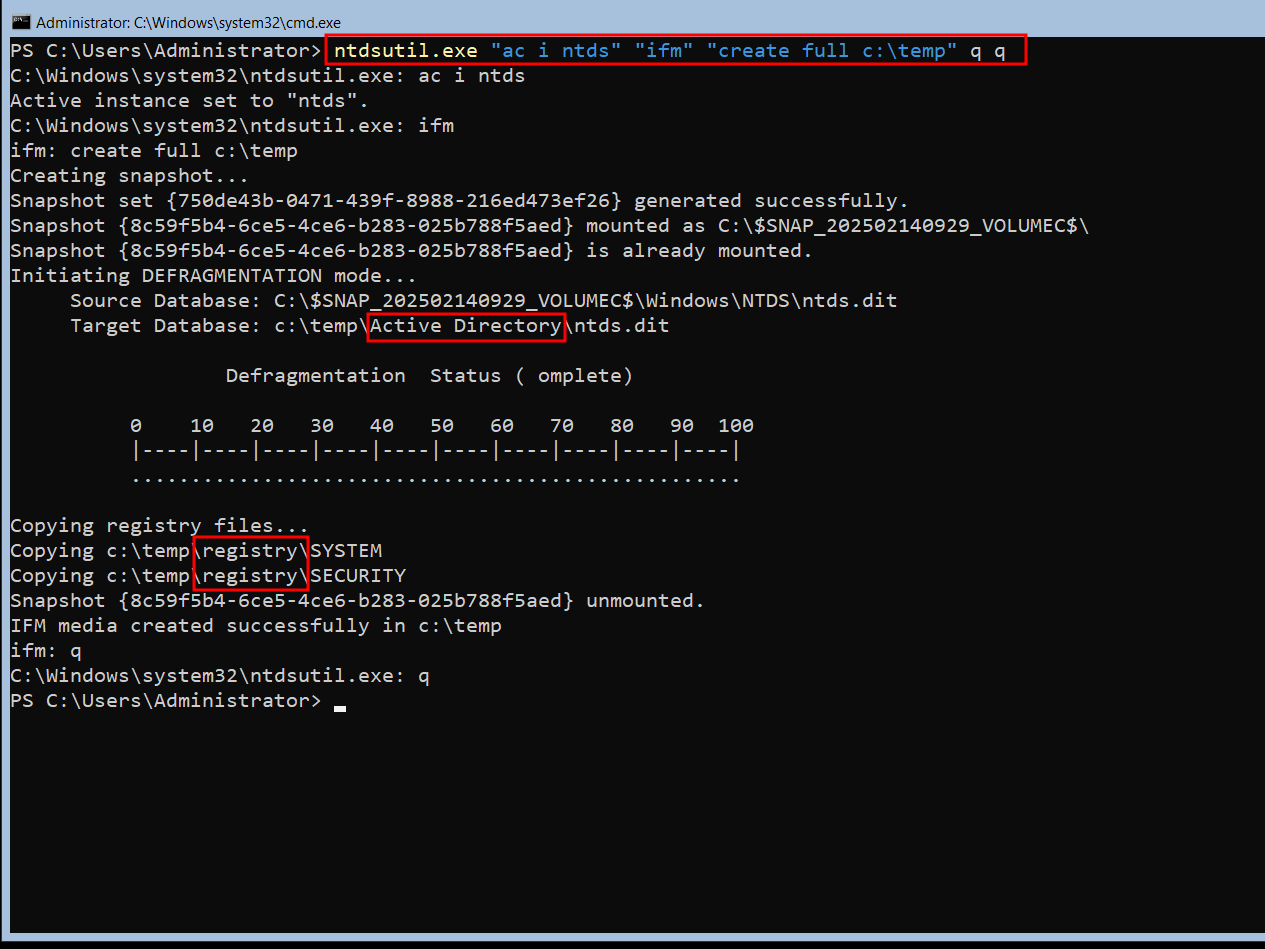
When NTDSUTIL is used to create a snapshot, it generates these two folders in the same directory. These folders are temporary and are used to store the snapshot data. Here’s why they’re significant:
- “Active Directory” Folder: This folder contains the NTDS.dit file and other related AD database files.
- “registry” Folder: This folder contains registry hive files that are necessary for the snapshot process.
The presence of these two folders together is highly unusual in a normal environment. Legitimate use of NTDSUTIL by administrators is rare, and when it does happen, it’s usually in a controlled and monitored context. Therefore, if you spot these folders being created together, it’s a strong indicator that someone is trying to dump the NTDS.dit file.
How to Detect This Activity
Now that we know what to look for, let’s talk about how to detect the creation of these folders.
1. File System Monitoring
- Use tools like Sysmon or Windows Event Logs to monitor for the creation of folders named “Active Directory” and “registry” in the same directory.
- Look for events like
4656(A handle to an object was requested) or4663(An attempt was made to access an object) in the Windows Security Log.
2. SIEM Alerts
- Configure your SIEM (Security Information and Event Management) system to alert on the creation of these folders. For example, in Splunk, you could create a search query like:
index=windows EventCode=4656 (ObjectName="*\\Active Directory" OR ObjectName="*\\registry") | stats count values(ObjectName) as CreatedFolders by _time, ComputerName, User | where count = 2 AND mvcount(CreatedFolders) = 2 - This query ensures that both folders are created in the same directory, reducing false positives.
3. Sigma Rule for Detection
-
Here’s a simplified Sigma rule to detect the co-creation of “Active Directory” and “registry” folders:
title: Detection of NTDS.dit Dumping via Co-Creation of "Active Directory" and "registry" Folders description: Detects the co-creation of "Active Directory" and "registry" folders in the same directory, which is indicative of NTDS.dit dumping using NTDSUTIL. author: Amr Fathy date: 2025/02/14 references: - https://attack.mitre.org/techniques/T1003/003/ (Credential Dumping: NTDS) tags: - attack.credential_access - attack.t1003.003 logsource: product: windows service: security detection: selection_1: EventID: 4656 # A handle to an object was requested (file creation) ObjectName|contains: '\Active Directory' selection_2: EventID: 4656 ObjectName|contains: '\registry' condition: selection_1 and selection_2 falsepositives: - Legitimate administrative activity (rare) level: high -
This rule triggers only if both folders are created, making it highly specific to NTDS.dit dumping activity.
Hypothetical Scenario:
You’re a SOC analyst, and your SIEM suddenly lights up with alerts for the creation of “Active Directory” and “registry” folders on one of your Domain Controllers. You quickly investigate and find that the folders were created in C:\temp, a directory that’s rarely used. You also notice that the ntdsutil.exe process was executed around the same time.
You immediately isolate the affected Domain Controller from the network and begin your incident response process. By catching this activity early, you’ve potentially stopped an attacker from exfiltrating the NTDS.dit file and compromising your entire domain.
So, the next time you see those two folders pop up together, don’t panic—but do act quickly. Your domain might just depend on it.
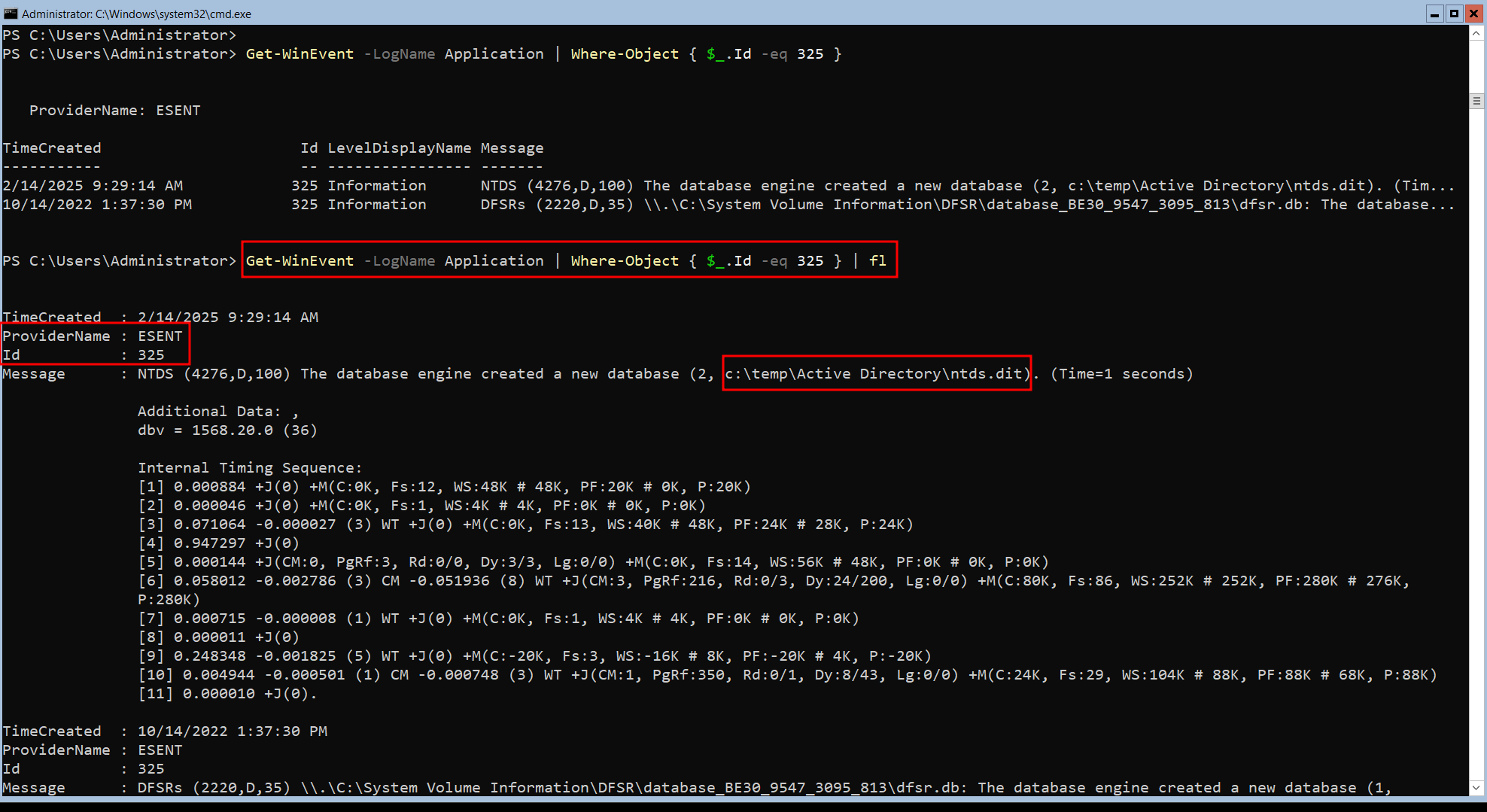
UPDATE - 2025/02/15:
I’ve found that there is an Event ID 325 in Application Event Log which indicate a change in NTDS.dit database location, which can be used as an alternative way to detect this attack as in the following screenshot.
References:
- https://www.ired.team/offensive-security/credential-access-and-credential-dumping/ntds.dit-enumeration
- https://attack.mitre.org/techniques/T1003/003/